How Domain History Ownership Data Enriches Threat Intelligence
Threat actors often register domain names in bulk. So when a malicious website gets blacklisted, they still have loads of backup domains. For this reason, domain names are a valuable source of threat intelligence. Organizations can further enrich this particular intelligence source by looking into domain history ownership records.
With historical WHOIS data, more context is given to domain intelligence, making crucial business processes such as third-party risk assessment, cybersecurity implementation, and cybercrime investigations more effective. Let us explain.
What Is Domain History Ownership?
Domain names are virtual world commodities that are regularly being traded. When someone is interested in a domain name that someone else already owns, he/she can offer to buy the specific domain. On the other hand, when a domain owner lets a domain name expire, anyone can grab and register the domain name for his/her use.
As such, one can imagine the history of domain ownership of a 10-year-old domain name. Such records contain the ownership records provided by its past owners. Domain history ownership includes the following registrant data:
- Name
- Organization name
- Street address
- City/State/Country
- Email address
- Phone number
In essence, it is like doing a backdated WHOIS lookup as the data points you retrieve are the same ones you get from a WHOIS lookup.
Why Is the History of Domain Ownership Important?
Historical WHOIS data is valuable, especially in light of the current privacy redaction of WHOIS records. When you perform a WHOIS lookup on a domain today, you would most likely encounter registrant data that has been “redacted for privacy,” “General Data Protection Regulation (GDPR)-masked,” or protected by a privacy protection service company.
However, when you have access to the history of domain ownership, you would have an inkling about who owns the domain, if there were no recent ownership changes of course.
Consider the domain breakingnewsenglish[.]com as an example. We randomly selected this domain name. WHOIS lookup results reveal that its owner uses the privacy protection service of Domains By Proxy, LLC.
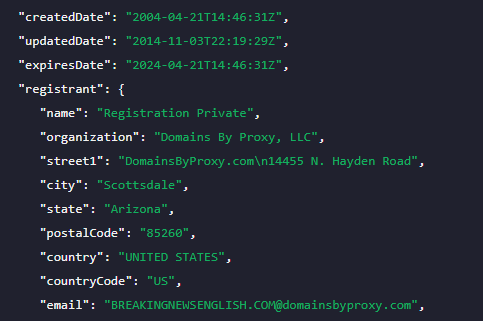
It also tells us that the WHOIS record was last updated on 3 November 2014. If we can get our hands on the domain history ownership data for that specific period, we might be able to determine its current owner.
Domain Name Stat has been tracking domains since 2008. And it revealed that the domain’s owner started using Domains By Proxy in 2017. The registrant since 2012 is someone named S. Banville with an address in Japan.
How Can Domain History Ownership Data Enrich Threat Intelligence?
The domain name above was randomly selected to illustrate why domain history ownership data is essential. But imagine if you’re dealing with more nefarious or at the very least suspicious domains. You can take threat intelligence to a whole new level with the help of WHOIS history.
For instance, what do organizations usually do when they are alerted to an alleged cyberattacker? The best practice would be to block all of the domain names the attacker owns. But with the redaction of WHOIS records, as illustrated in the previous section, this practice might get difficult.
To better illustrate how domain history ownership can help enrich threat intelligence, here is an illustration for third-party vendor risk management.
An Illustration: History of Domain Ownership Identification for Third-Party Risk Management
Third-party cyber risks are more severe than some organizations care to admit. But in recent years, it has become too big to ignore. The Facebook data leak of about 540 million records in 2019, for instance, was attributed to a third-party service.
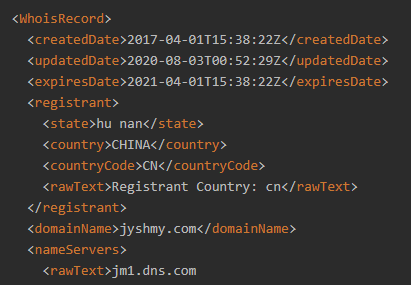
It pays to scrutinize every vendor or third party before you allow them access to your network. Let’s take a hypothetical surgical mask supplier with the domain jyshmy[.]com as an example. A typical vendor risk assessment could involve these processes:
- Check WHOIS records: WHOIS lookup results look innocent enough, as the domain has been
around since 2017. There is nothing suspicious in the fact that there its registrant’s name has been
redacted. The WHOIS record further states that the registrant has an address in Hunan, China, which is
consistent with the information given by the supplier.
- Perform a background check: This process could involve checking the supplier’s website, looking for client feedback, and checking government databases to verify its legitimacy. You may also want to run the domain on virus detection engines or blacklist databases. For jyshmy[.]com, VirusTotal didn’t reveal any malicious or suspicious ties.
If the supplier passes these checks, organizations can then transact with them. The supplier can send them emails that employees deem trustworthy. But what if we add checking domain history ownership as another step in the vendor assessment process?
A WHOIS history lookup reveals that jyshmy[.]com was once owned by an individual named Fujie Wang. The name and address match one of the Federal Bureau of Investigation (FBI)’s most wanted cybercriminal, who was indicted for being part of a hacking group that targeted large businesses in the U.S.
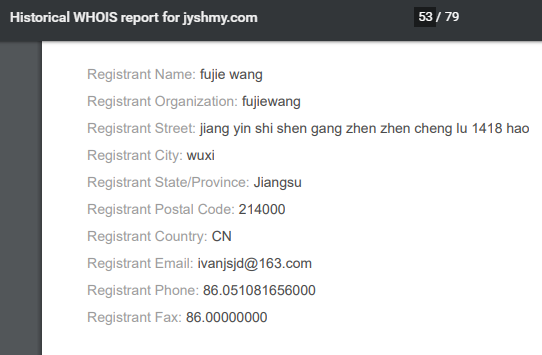
The domain jyshmy[.]com could be one of the malicious domains that Wang, or someone who happens to share the same name, used at that time. And since the cybercriminal is still at large, there is a possibility that he still owns the domain. As such, organizations must be careful in dealing with jyshmy[.]com and other domains that were once possibly owned by individuals like Fujie Wang.
Other Domains with a Shady History of Domain Ownership
Fujie Wang is not the only attacker who has owned several domains in the past. Domains are widely used as weapons by cybercriminals, so this comes as no surprise. For one, we see Ehsan Mohammadi as the past registrant of over a hundred domain names, including the following:
- em-counsel[.]co[.]uk
- iparkexpo[.]com
- geoteem[.]com
- golestaneh-art[.]com
- ismspanel[.]com
Ehsan Mohammadi is one of the nine Iranians indicted for wire fraud, computer intrusion, and identity theft. He was believed to be working for the Iranian government and remains wanted by the FBI.
Igor Turashev is also the elusive technical brain behind Evil Corp’s operations. His name can be seen in the historical WHOIS record of the domain sofronov[.]com, which has been on sale since January 2018. Evil Corp is the cybercrime group that notably used Dridex banking Trojans to steal millions of dollars from their victims.
Beyond Third-Party Risk Assessment
Besides third-party risk management, domain history ownership is valuable in cybercrime investigations as well since it helps experts create attacker profiles. Furthermore, investigators can better track attackers’ digital footprints even though their current WHOIS records are redacted.
WHOIS history further helps organizations with their brand protection efforts as it allows them to see a domain’s past associations before purchasing it. Cybersecurity tools that obtain intelligence from domain history ownership records are also more robust and effective in protecting users’ networks.
We only cited three cyber attackers who have a history of domain ownership. There could be hundreds more, and it’s challenging to keep track of them manually. As such, sources that provide historical domain records are useful. A domain’s past could give valuable insights to cybersecurity teams, third-party risk managers, and cybercrime investigators, to name a few.
Read the other articles Domain Name Stat
Domain Name Stat